Secure and Flexible: Whitelisting in IoT Networks
In an era where digital transformation is not just an option but a necessity, securing network communications in the Internet of Things (IoT) becomes paramount. You might be familiar with basic security measures like firewalls and encryption, but have you heard about the critical role of whitelisting in safeguarding your LoRaWAN® networks? While many are acquainted with the concept in the context of Basic Station mode, our approach extends this crucial security feature to Packet Forwarder mode—a game changer in network management.
This unique capability enhances security and fine-tunes operational efficiency, setting a new standard for what businesses can expect from their IoT infrastructure. Whether you’re managing a small fleet of sensors or a vast array of industrial IoT devices, understanding how whitelisting works and why it’s indispensable could redefine how you protect and streamline your operations.
What is Whitelisting in General and in the Context of LoRaWAN Communication?
Whitelisting serves as a critical defense mechanism, much like a bouncer at a high-profile event, ensuring only approved guests can enter.
Generally, whitelisting refers to the practice of allowing access to network services, applications, or devices based exclusively on their inclusion in a pre-approved list. This is in stark contrast to blacklisting, where entities are denied access based on a list of known undesirables. The strength of whitelisting lies in its proactive approach—instead of reacting to threats, it prevents them from engaging with the system in the first place.
In the specific context of LoRaWAN—a popular low-power, wide-area networking protocol designed for IoT—whitelisting takes on a pivotal role in managing device connectivity and security. LoRaWAN networks facilitate communication among scattered devices over long distances, often in challenging environments that demand robust security to prevent unauthorized access and data breaches. Here, whitelisting ensures that only devices with verified identities can connect to and communicate through the network. This is not just a matter of securing data but of optimizing network performance and reliability by reducing the risk of interference from rogue devices.
The typical whitelisting implementation in LoRaWAN systems has been mostly confined to Basic Station mode. Basic Station is a type of LoRaWAN gateway architecture that provides streamlined management and secure data routing between end devices and network servers. It incorporates whitelisting as a standard security measure, checking device credentials against a list maintained by network administrators before allowing access to the network.
However, our approach extends this essential security feature beyond the conventional use in Basic Station mode to include Packet Forwarder mode. Packet Forwarder mode allows a more flexible network setup, acting as a bridge that forwards raw data packets from end devices to a network server without parsing or processing the content. This mode typically allows for broader device compatibility and is easier to deploy at scale but is perceived as less secure due to its open nature.
By integrating whitelisting into Packet Forwarder mode, we not only retain its deployment advantages but significantly enhance its security posture, providing peace of mind for businesses that require both flexibility and stringent security controls in their IoT deployments.
How Did We Achieve This?
By rethinking how packet forwarding can work in harmony with advanced security measures, we developed a system that filters device communications at the packet level based on their credentials. This means every data packet a device sends is checked against a whitelist before being forwarded to the network server. If the device isn’t on the list, its data goes nowhere. Think of it as a highly selective mailroom that only sends along letters from recognized senders.
While the concept of whitelisting isn't new, its application in Packet Forwarder mode is quite revolutionary. In Basic Station mode, whitelisting is more straightforward because the architecture inherently supports more rigorous security protocols. The challenge was bringing that level of security to Packet Forwarder mode without sacrificing its operational benefits.
In achieving this, we've provided an answer to a critical industry dilemma: How do you maintain the ease and flexibility of Packet Forwarder mode while ensuring the network remains impenetrable to unauthorized devices? Our solution ensures that every device in the network is authenticated and authorized, thereby mitigating potential risks associated with open access, such as data breaches or network interference.
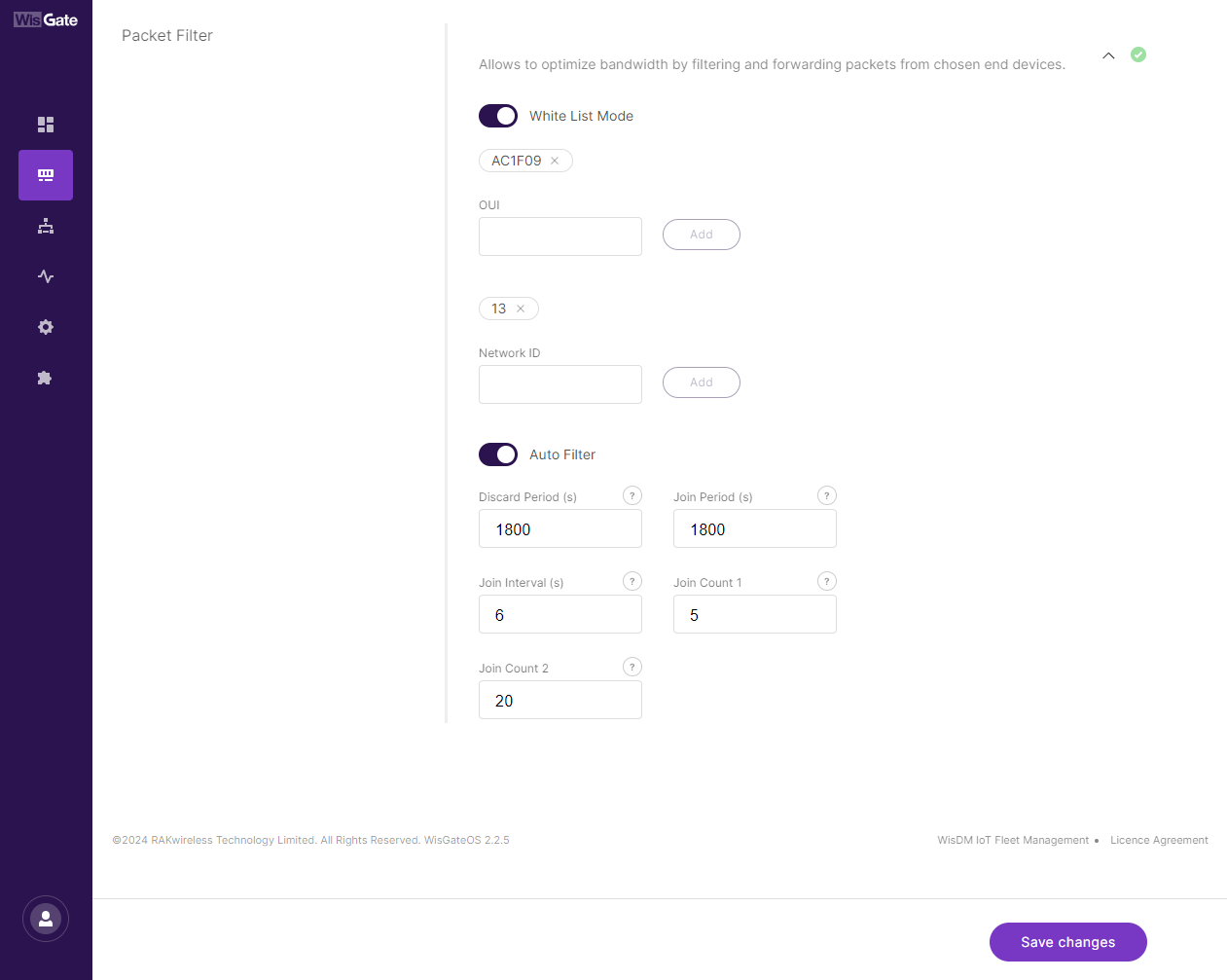
What Challenges Does Whitelisting Tackle?
In IoT, where countless devices communicate and interact across expansive networks, several pervasive challenges threaten the stability and security of these digital ecosystems. But how exactly does whitelisting in Packet Forwarder mode address these concerns? Let's peel back the layers to understand the tangible issues this feature mitigates.
- Unwanted Network Traffic and Congestion: One of the foremost challenges in managing a sprawling IoT network is the sheer volume of data that flows through it. Without strict access controls, this traffic can become not just a stream but a deluge, overwhelming network resources and leading to congestion. By implementing whitelisting, we effectively put a filter in place—think of it as a highly selective sieve that ensures only relevant and authorized data packets make it through. This targeted filtering significantly reduces unnecessary network traffic, alleviating congestion and enhancing the overall efficiency and responsiveness of the network.
- Security Vulnerabilities: The open nature of Packet Forwarder mode, while advantageous for ease of deployment and operational flexibility, traditionally opens up vulnerabilities. Unauthorized devices could potentially connect and transmit harmful or irrelevant data, posing a serious security risk. Whitelisting acts as a robust barrier, a kind of digital gatekeeper, ensuring that only devices with verified credentials can access and operate within the network. This not only helps in protecting against external threats but also reduces the risk of internal mishaps, where misconfigured or malfunctioning devices could disrupt network operations.
- Resource Mismanagement: IoT networks, particularly those spanning vast geographical areas, rely heavily on the efficient allocation and usage of resources. Without whitelisting, devices can hog bandwidth or prioritize traffic in a way that isn't optimal for the network’s overall health. By ensuring that only pre-approved devices are connected, whitelisting helps maintain a more controlled and equitable distribution of network resources. This is crucial for maintaining service quality across all endpoints and for all users.
- Compliance and Regulatory Challenges: As industries increasingly adopt IoT solutions, compliance with regulatory standards becomes paramount. Uncontrolled device access can lead to sensitive data breaches, violating regulations such as GDPR (General Data Protection Regulation) in Europe or HIPAA (Health Insurance Portability and Accountability Act) in the United States. Whitelisting in Packet Forwarder mode not only tightens security but also provides a verifiable method of enforcing compliance, ensuring that every device on the network is known and authorized according to the latest standards.
What Benefits Does Whitelisting Bring?
Having explored the challenges that whitelisting addresses, it’s crucial to understand the direct benefits that this feature brings to LoRaWAN networks, especially when implemented in Packet Forwarder mode. These advantages not only enhance network performance and security but also provide substantial operational and cost efficiencies that are critical for businesses looking to optimize their IoT strategies.
- Enhanced Network Security: The primary benefit of implementing whitelisting is the significant uplift in network security. By ensuring that only pre-approved devices can connect, networks are shielded from a range of threats, including unauthorized access and potential attacks. This rigorous control creates a fortified barrier against external threats and mitigates risks associated with device spoofing and other forms of cyber intrusion. For businesses, this means less downtime due to security breaches and stronger protection of sensitive data, aligning with stringent compliance standards.
- Reduced Operational Costs: Whitelisting reduces unnecessary network traffic, which directly translates to lower operational costs. Networks free from unwanted data transmissions use less bandwidth and require less processing power, which can substantially decrease the costs associated with data management and transmission, particularly in systems that rely on cellular data connections. Moreover, with a more streamlined network, maintenance and troubleshooting become less frequent and less complex, further reducing operational expenses.
- Improved Network Efficiency and Reliability: By filtering out unauthorized devices and data, whitelisting ensures that network resources are utilized efficiently. This optimized use of bandwidth and reduced congestion lead to improved network performance, with faster response times and fewer service interruptions. For IoT deployments in critical environments, such as healthcare or industrial automation, reliability is a must. Whitelisting enhances this reliability, ensuring that essential data is transmitted promptly and accurately across the network.
- Simplified Compliance and Governance: For many industries, adhering to regulatory standards is not just best practice but a legal requirement. Whitelisting aids in compliance by providing a clear audit trail of which devices are allowed to connect and communicate within the network. This traceability is crucial for meeting security audits and adhering to regulations such as GDPR, HIPAA, or others specific to industries like finance or healthcare. Simplified compliance means fewer legal risks and potential fines, contributing to a stronger and more sustainable business model.
- Increased Visibility and Control Over IoT Devices: Integrating whitelisting into Packet Forwarder mode offers unparalleled visibility into network activity, allowing administrators to monitor which devices are connected and how they are interacting with the network. This level of control is vital for managing large-scale IoT deployments, enabling precise management of device functionalities and the ability to respond swiftly to any anomalies or performance issues.
Illustrating the Added Value: Why Our Whitelisting in Packet Forwarder Mode Is Impactful
When businesses consider deploying IoT solutions, the flexibility to adapt to diverse environments and the assurance of robust security are often at the top of their requirements list. Our unique whitelisting implementation in Packet Forwarder mode addresses these needs, providing a compelling value proposition for industries that cannot afford to compromise on either.
Traditionally, increasing flexibility in IoT networks has meant compromising on security. However, our innovative approach flips this notion on its head. By incorporating whitelisting directly into Packet Forwarder mode, we ensure that each device connected to the network is meticulously vetted and authorized. This not only prevents unauthorized access but also significantly mitigates the risk of data breaches and cyber-attacks, which are becoming increasingly sophisticated. For industries handling sensitive information, such as healthcare or finance, this means they can expand their IoT deployments confidently, knowing their data is secure.
In conclusion, our unique implementation of whitelisting in Packet Forwarder mode sets a new standard in the IoT landscape. By merging unparalleled security with operational flexibility, our solution addresses the critical needs of modern businesses across various industries. The enhanced security framework prevents unauthorized access and ensures compliance, while the operational efficiencies drive down costs and streamline network management.
This innovative approach secures networks and empowers businesses to leverage IoT technology without compromise. As we continue to innovate and refine our solutions, we invite you to join us in redefining what is possible with IoT deployments.
Reach out to our team to explore how our advanced whitelisting features can transform your IoT strategy and help you achieve new levels of efficiency and security.



